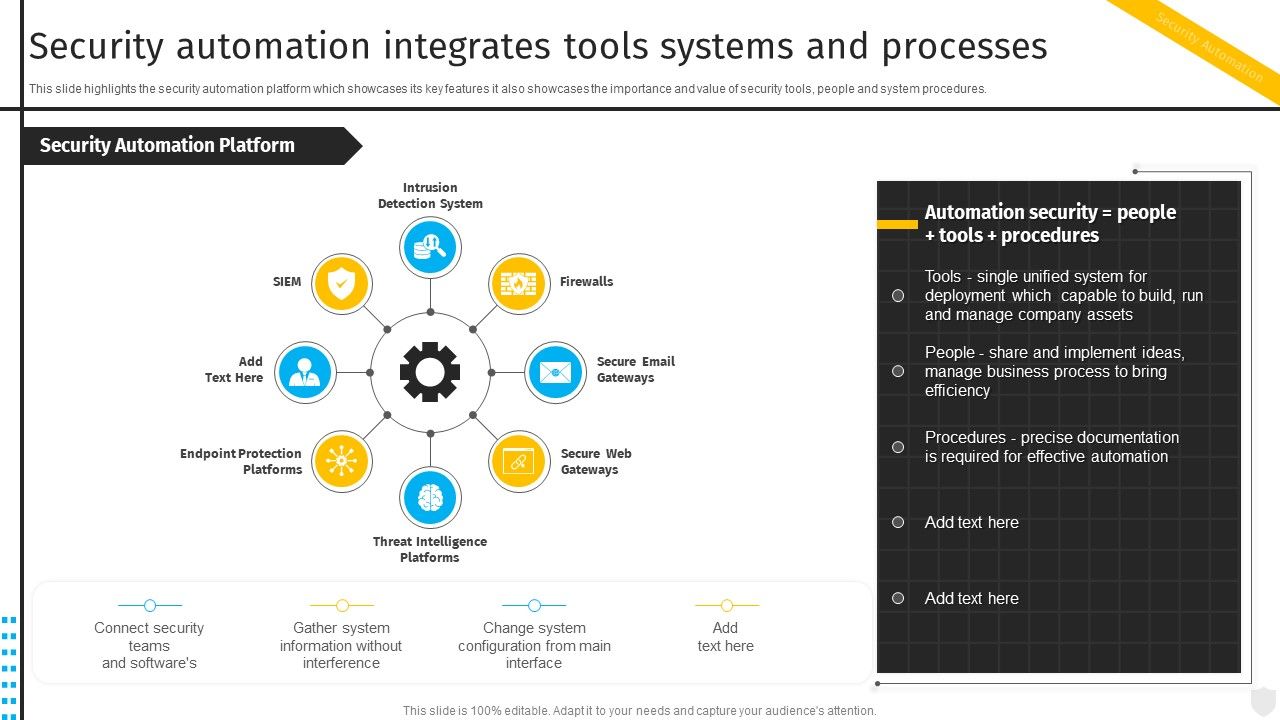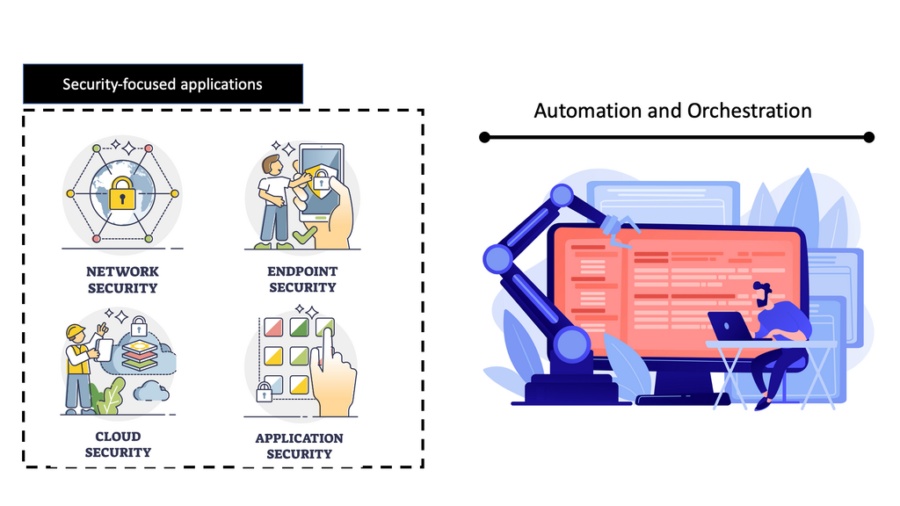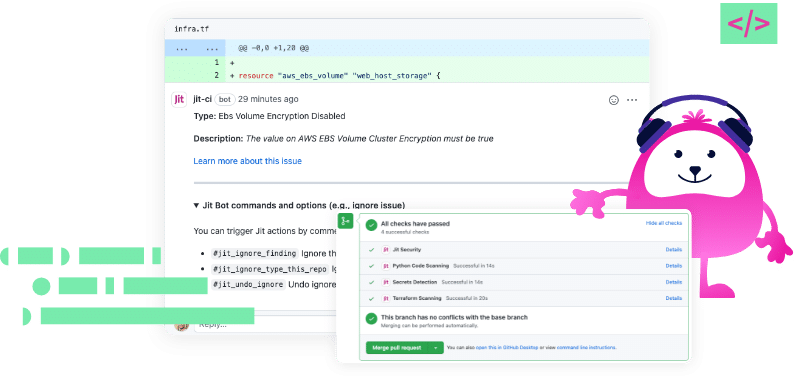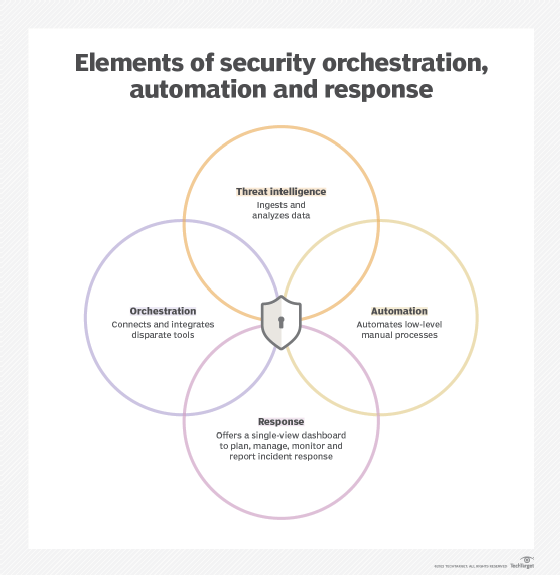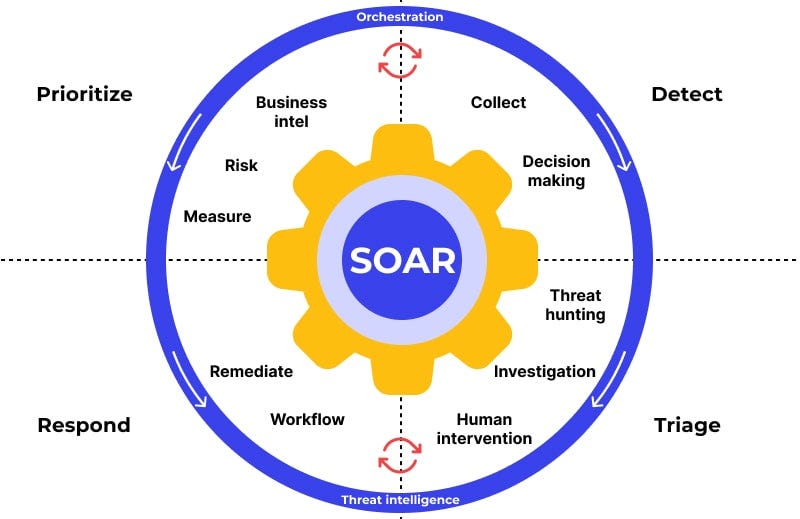
SOAR (Security Orchestration Automation and Response) Definition, Best Practices and Tools | by 0xffccdd | Medium

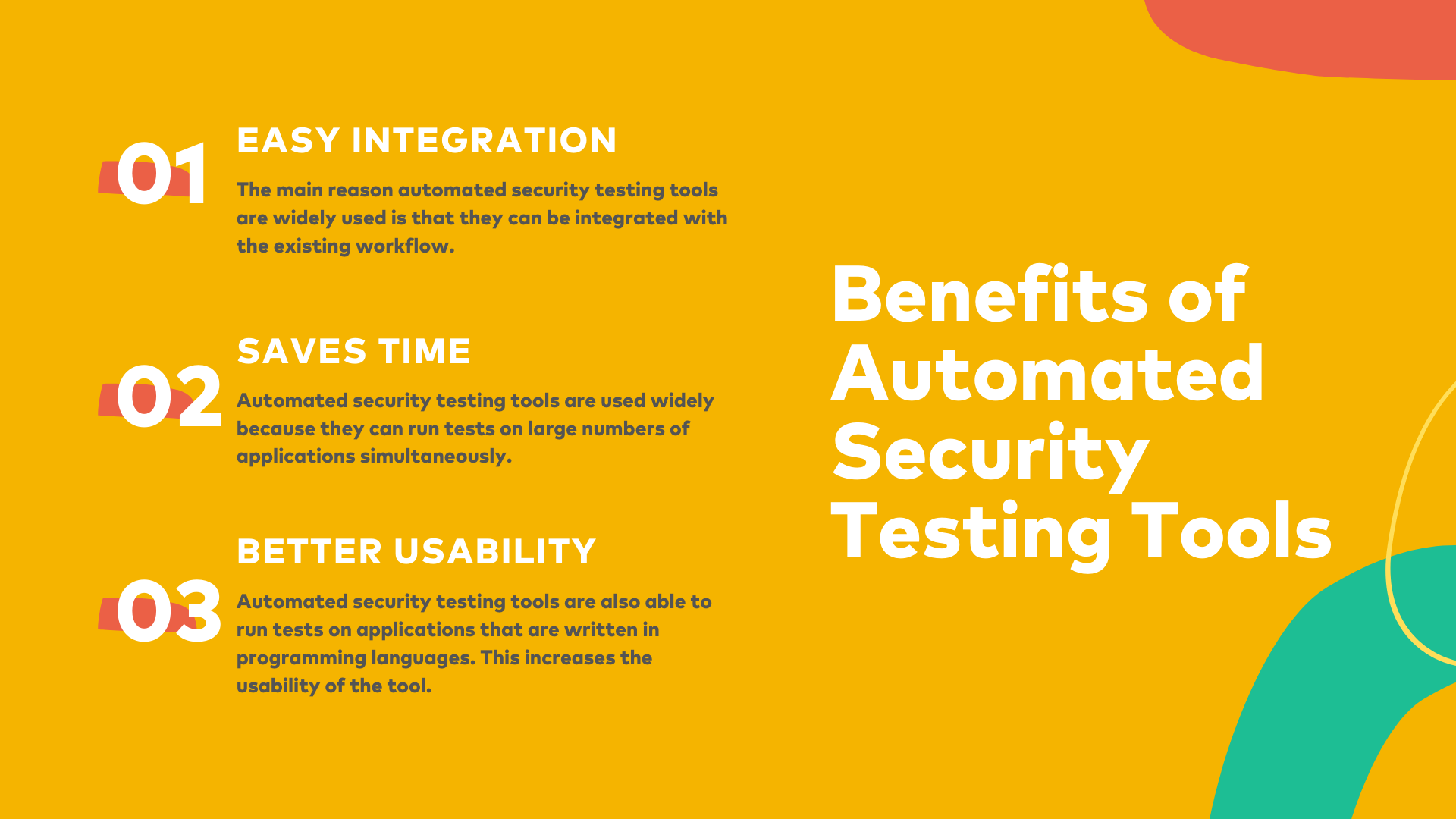
Practical Security Automation and Testing: Tools and techniques for automated security scanning and testing in DevSecOps 1, Hsu, Tony, eBook - Amazon.com